When I was working as Configuration Manger Support Engineer for Microsoft I get multiple calls about issues related to client machines pulling content from wrong distribution point. This issue can create major network congestion especially on small remote sites that have slow connection. I would start by explaining basic terms like boundary and boundary groups.
Boundary is network location within an intranet. It is logical grouping of clients in group using either IP subnet, IP address range, active directory site name, IPV6 prefix and VPN starting with configuration manager 2006. Boundaries created by themselves doesn’t serve any purpose unless they are added to boundary groups.
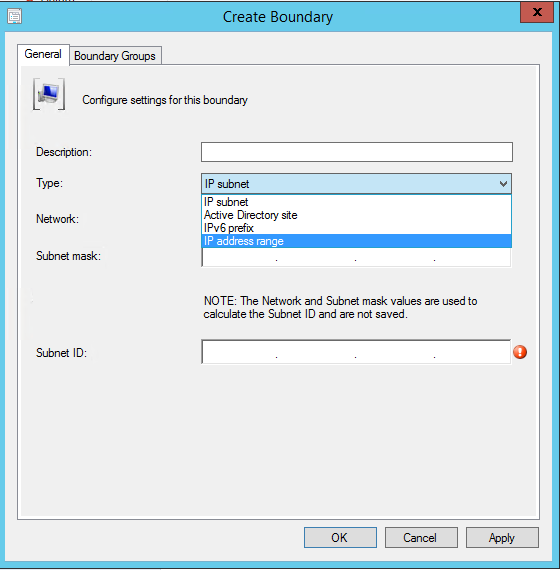
Boundary Group is logical grouping that we use to group Boundaries together. Client machines use boundary groups to find site assignment and locate site system roles they can use for different configuration manager tasks.
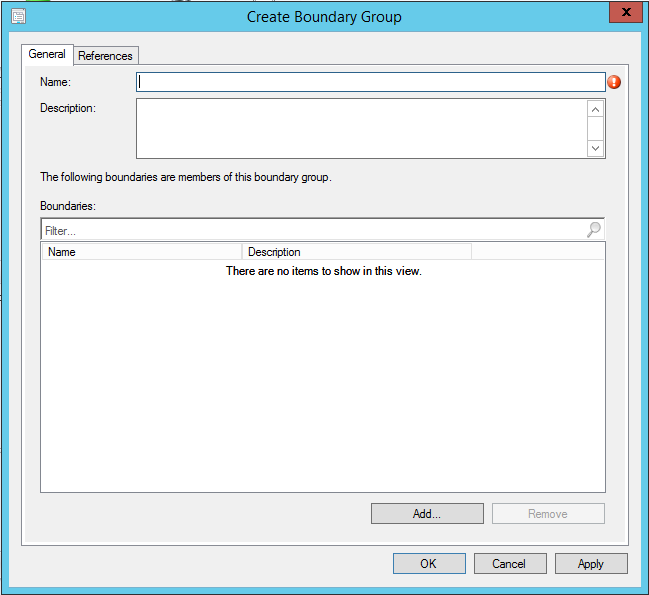
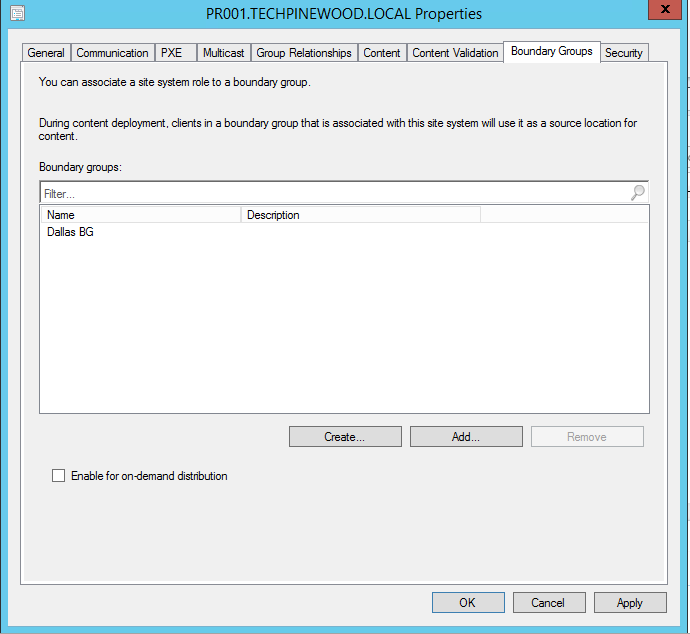
Distribution points are one of the site system roles that depend on “Boundary Groups”. Once “Boundary Groups” are created they would need to be added to the distribution points.
Majority of the issues related to client pulling content from the wrong distribution point is related to overlapping boundaries. We have to make sure that each boundary is not member of multiple boundary groups with different site assignments. Most of the time this happens when we have boundary created based on more than one type of boundary . If you decide to create boundary based on IP address range then unless you require avoid using other types like boundaries created using active directory site name. The action of creating boundaries using different types is definitely supported but it would add the administrative burden of keeping boundaries from overlapping.
I would demonstrate the concept using the network diagram shown below for the company that we are going to call TECHPINEWOOD INC.
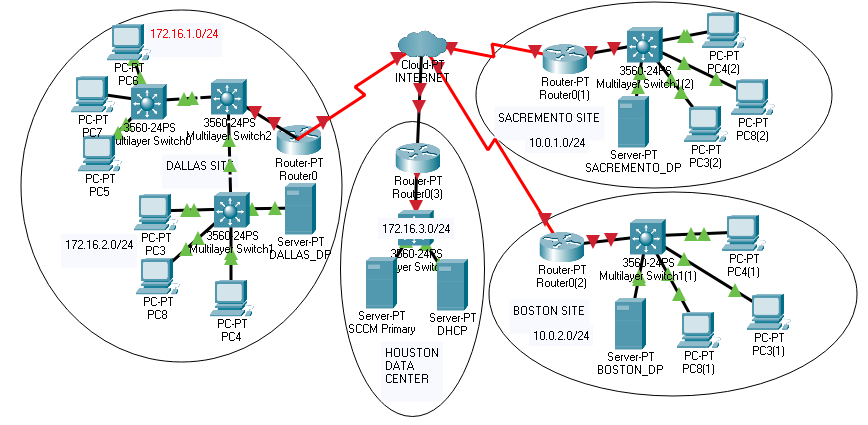
TECHPINEWOOD INC has the following items
- TECHPINEWOOD INC has four sites. The sites are Dallas which is the Headquarter, Houston data center, and two remote sites Sacramento and Boston.
- Dallas HQ has two subnets that it uses for two buildings. The subnets are 172.16.1.0/24 and 172.16.2.0/24.
- Houston Data center has the subnet 172.16.3.0/24. This is the site where the Primary site server is located.
- Sacramento remote site has one subnet 10.0.1.0/24.
- Boston remote site has one subnet 10.0.2.0/24.
- We have the cloud in the middle which is the Public internet or WAN which interconnects the multiple sites.
I would start designing the boundary groups for the Dallas Headquarter. Now this site has two IP subnets. I would start by creating two boundaries using “IP address Range”
boundary1 – 172.16.1.1-172.16.1.254
boundary2 – 172.16.2.1-172.16.1.254
Now I have left the .0 and .255 which are the first IP address and last IP address of these range since in production these IP addresses are reserved for the subnet and broadcast address for that subnet. If you include these two IP addresses in your definition it won’t affect your boundary but I chose to omit it as personal preference.
Next step is I would create boundary group called “DALLAS_BG” and add the two boundaries boundary1 and boundary2 to the “Dallas_BG” boundary group.
The last step is to add this boundary group “Dallas_BG” to the local DP for the Dallas site and I have named it “Dallas_DP” on the network diagram.
Now lets discuss some scenario based issues that might arise here.
Scenario 1- All the client machines belong to one Active directory site. what would happen If admin defines new boundary based of type Active directory site and adds the new boundary to the boundary group “Dallas_BG” ? In this case the client machines could pull content from any of the remote sites. If the content that the clients are looking for doesn’t exist on the local Dallas DP then the client would try to pull the content from remote sites. This is one example of bad boundary design.
Lets move on to the next site in this case the Houston Data center. You don’t really have any clients in this site. Now you have primary site in these subnet inside the data center. It might have DP role with the primary site and might want to use it to supplement one of the local DPS for the other sites. These really depends on how your network is designed. If you would like the other sites pulling the content from the primary site DP then you can create Boundary for the group called boundry3 and with the range 172.16.3.1 -172.16.3.254 and add this boundary to any boundary group defined for the remote sites and you would like to those remote sites to be able to pull content from the primary site DP. You could also choose not to have any DP role on the primary site and remove the role and use the local DPS.
Now lets take a look at the remote Site of Sacramento. It has one IP address subnet 10.0.1.0/24. Boundary and boundary group would be defined like this.
boundary4 – 10.0.1.1-10.0.1.254
Create boundary group called “SACRAMENTO_BG” and add boundary4 to the boundary group.
Scenario 2-What would happen if new admin comes in and add boundary1 to “SACRAMENTO_BG” ? The client machines in Dallas would able to pull content from the “SACRAMENTO_DP” over the WAN link. This usually happens if content happens to be distributed only to the “SACRAMENTO_DP” and not the “Dallas_DP” or the “Dallas_DP” is temporarily out of service. This is still unwanted result. Therefore we have to pay attention to what boundaries belong to Boundary group.
Finally the Boston Site. It has one subnet 10.0.2.0/24. We would create the boundary and boundary groups as follows.
boundary5 – 10.0.2.1 – 10.0.2.254
Create boundary group called “BOSTON_BG” and add boundary5 to “BOSTON_BG”
In conclusion your design choice depends upon your environment and what you need to achieve. The best practice is to keep the fewest boundaries that meet your need and avoid creating overlapping boundaries.