🔍 Vulnerability Research with PinewoodSec
Exploring modern web security threats with practical demos and CVE deep dives.
🚀 About the Project
PinewoodSec is our initiative to showcase real-world vulnerability research with hands-on demos. From authentication bypasses to file inclusion and RCEs, each lab is designed to help you learn through doing.
Whether you're a student or professional, PinewoodSec offers a practical way to explore CVEs, exploit chains, and secure coding practices.
🎯 Demo Objectives
- Understand CVE-2025-24813: Tomcat Path Equivalence RCE
- Learn to identify and exploit path traversal bugs
- Build your own vulnerable lab (PinewoodStore)
- Practice mitigation techniques in real code
As Vulnerability and Patch management engineer I have used many tools to investigate and remediate vulnerabilities that have been identified on systems in the Environment. Tenable has vulnerability Sc...
I have setup a Networking Lab in Google Cloud using EVE-NG and Ubuntu image that was specifically created for Deploying EVE. The setup is pretty straight forward as long as you follow the instructions...
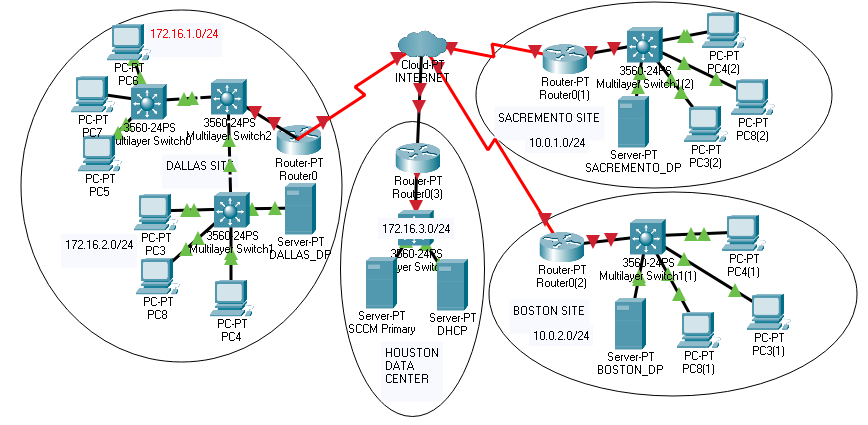
When I was working as Configuration Manger Support Engineer for Microsoft I get multiple calls about issues related to client machines pulling content from wrong distribution point. This issue can cre...
When it comes to enabling PXE for distribution points in Configuration Manager I get a lot of support questions with regard to what is best practice for setting up PXE for distribution points. The mai...